????????????????
Nowadays, computers play a huge role in everyday life. But did you know that computer threats are increasing as well? One of the most frightening threats is the threat posed by computer viruses. Which is becoming more and more intense in the destruction. And some users do not have the knowledge to check whether their machines are infected or not.
????????????????
Nowadays, computers play a huge role in everyday life. But did you know that computer threats are increasing as well? One of the most frightening threats is the threat posed by computer viruses. Which is becoming more and more intense in the destruction. And some users do not have the knowledge to check whether their machines are infected or not.
Compiled by : Kitisak Jirawannakul
Source : ThaiCERT: Thai Computer Emergency Response Team, Computer Security Coordination Center, Thailand
Published on : 1 April 2003
Currently, computers play a large role in everyday life. But did you know that computer threats are increasing as well? One of the most frightening threats is the threat posed by computer viruses. Which is becoming more and more intense in the destruction. And some users do not have the knowledge to check whether their machines are infected or not. For this reason, the author has compiled this article. This article will discuss various attack characteristics of viruses and methods for checking to see if our machine is infected with a virus or not.
Note The word Malware comes from the word Malicious Software. It is a type of program that aims to destroy a computer system. Contains viruses Internet worms and Trojans in this article will use the term "Virus" which should be understood as meaning "Malware"
Let's start by studying the strategy of the virus.
It is well known that computer viruses aim to cause a system to malfunction. and is designed to have the ability to spread itself. Therefore, viruses must have different strategies. in order to be able to execute yourself in the system Most interesting forms of viruses are in the form of files such as games, animations, pornographic images or movies, etc. Nowadays, many files These mostly come in the form of files attached to e-mails. Victims or users lacking knowledge or caution will run these files without scanning them for viruses first. As a result, the machine you are using can become infected. In the following sections, we will discuss how to check if the machine you are using is infected and how to easily fix it.
When a virus infects memory
Memory-resident programs are programs that may be packaged and remains in the system's main memory after being executed. If the program is a virus, it will leave parts of the virus program in memory. To watch to see if an event that matches the conditions set by the virus causes the virus to continue working. For example, a virus that runs every March 20th (Date Trigger) or runs every time the user presses a button. "x" on the keyboard (Key Trigger) etc.
How to find out if there is a virus program embedded in the memory. It is necessary to use the Task Manager program, which is a tool that comes with every version of the Windows operating system. If it is a Windows 95/98/ME operating system, press the Ctrl-Alt-Del key to get the result as shown in Figure 1. And if it is a Windows NT 2000 and XP operating system, press Ctrl-Shift-Esc. The result will be as shown in Figure 2. From both pictures you can see that the Task Manager program will display a list of all processes running in memory. Therefore, if you are sure which process belongs to the virus Then terminate that process. By selecting the process that is sure to be a virus and pressing the End Task button for Windows 95/98/ME operating systems or pressing the End Process button for Windows NT 2000 and XP
Note Terminating a process that is believed to be a virus process may have the risk of causing undesired results, such as a Blue Screen of Death or other effects. Have the system restart, etc. Therefore, to be sure that a process may have to be studied from the operating system's manual first, whether it is a process of the operating system or a program that is being used or not. or search for information about that process in the internet If the search results do not indicate a virus process It should be left alone. To prevent risks that will occur
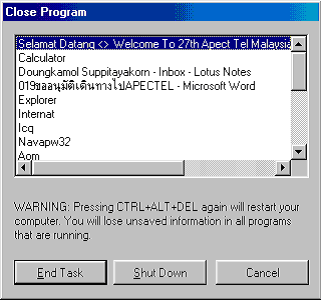
Figure 1 Task Manager program for Windows 98 operating system
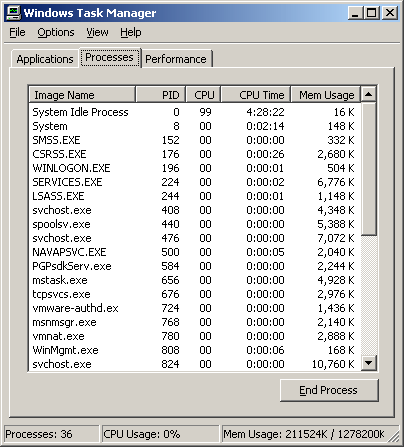
Figure 2 Task Manager program for Windows operating system 2000
Create a rogue process.
Viruses will attempt to use prominent and similar process names. with the names of common processes running on the machine In order to trick unsuspecting users into not daring to terminate the said process. This means that the virus will create a spoof process with a similar name. with general processes For example, WSOCK32.DLL is a common process. Go into memory to use the handle library of socket functions. and was renamed to WSOCK33.DLL Another example of a process that viruses often use to deceive is KERNEL32.DLL renamed to KERNE132.DLL (note that the L in KERNEL has been changed to a 1). But sometimes some viruses create a process. Sessions with the same process name but stored in different locations (different paths), such as KERNEL32.DLL Normally stored in a directory. %WindowsSystem32%, but some viruses create a process with the same name and store it in this directory. %WindowsSystem% can also be
Another way to detect rogue processes is Check for processes still running in memory using the method described in the previous section. A telltale sign that a computer has been infected with a virus is when a program is running and the program copies itself to run in memory. Even though at that time there was no such program running
If checking memory usage Most virus-based programs use almost all available memory. But if the above symptoms do not appear, you can be confident on another level that there is no virus currently running on the machine.
Dispersion control
From what has been said in the previous topic. How can a virus be embedded in memory? Needs to be executed first. Most virus executions are initiated by the user, whether intentional or not. The virus itself then uses other techniques. To ensure that it is executed at least once on every system, it places itself in the startup portion of the operating system. This is a very important step for the virus to be executed all the time and thus to remain embedded in memory. There are other techniques. that the virus uses to execute itself and embed it in memory other than this method
One technique that was popularly used in the early days. That is, the virus will infect the program used to interpret commands (Command Interpreter), which is mostly known as command.com. By infecting this file, it is guaranteed that the virus will be executed and embedded in Memory before the program interprets the command is executed, of course. Then to achieve the goal The virus adds itself to the autoexec.bat or config.sys file, which is a file that stores configuration settings used in DOS and is used to start basic Windows operations with
Registry
The virus later found a new way to embed itself in the system and be executed. This method involves editing values ??in the registry. The registry is where startup and customization settings are stored. Including various links of the program to be executed. Therefore, this position is the right location for the virus to implant itself in the system.
Finding out if there are viruses lurking in the registry. It will begin by running the program used to edit the registry by pressing the Start -> Run button. A dialog will appear as shown in Figure 3. Then type the word regedit in the Open: box. Select the OK button. From this step, the registry editing program window named regedit will appear as shown in Figure 4
Note Editing registry values ??is similar to terminating a process as described above. Which fixing it may lead to unwanted system problems. For example, a slight modification may make the system unable to be used or booted. And sometimes it may cause some programs to be unusable. Therefore, before editing values ??in the registry every time Must make a backup first. and must be carried out with caution
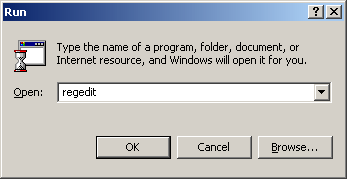
Figure 3 Dialogs are used to run any program.
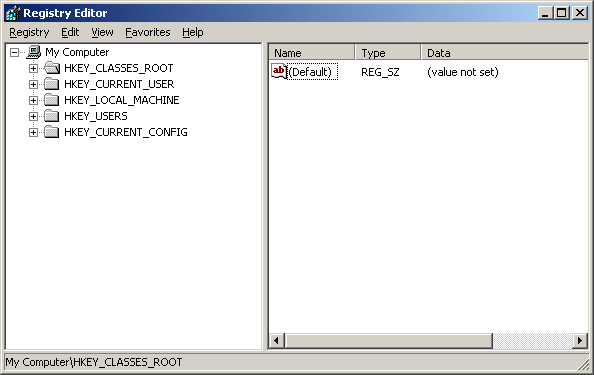
Figure 4 Registry editor window named regedit
In the regedit program, the Registry keys are in a column on the left that looks similar to The structure of files and folders in Windows Explorer in the location HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersion will have 3-6 folders in it. This is the part that is used to automatically initialize the registry. They are as follows
"Run"
"RunOnce"
"RunOnceSetup"
"RunOnceEx"
"RunServices"
"RunServicesOnce"
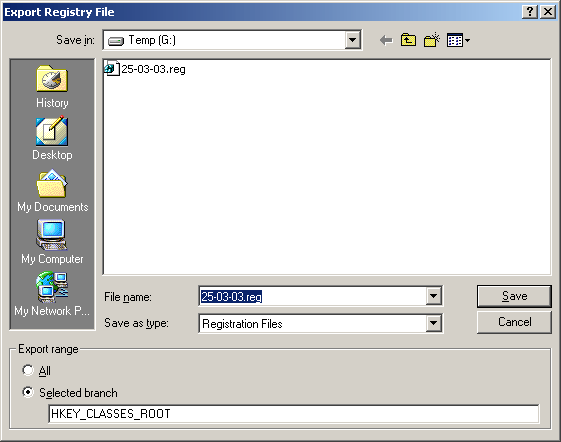
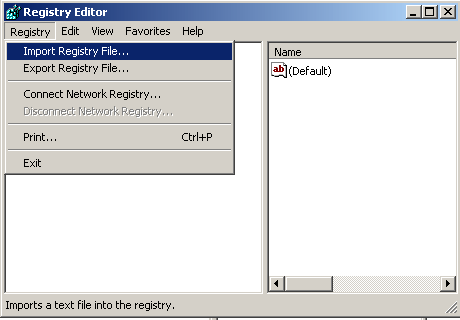
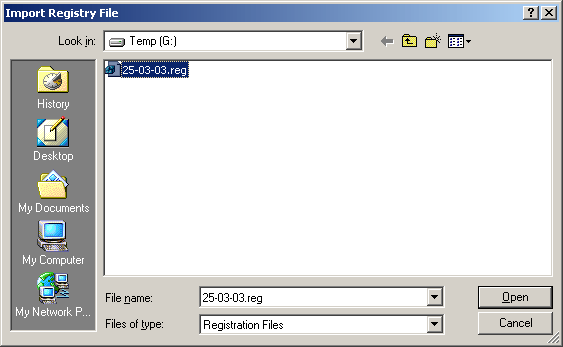
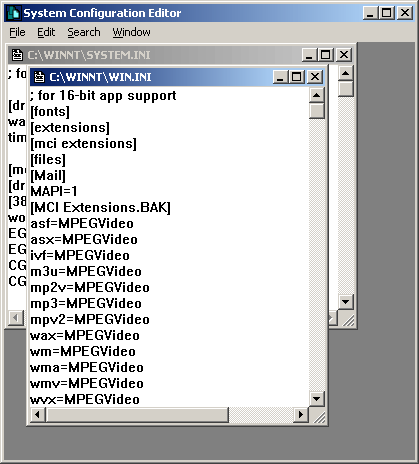
Which various applications The addresses in these folders are executed by the Windows operating system as soon as the system starts up. Additionally, another location that has 3-6 registry entries that are automatically started is in the HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersion When accessing the location of the registry key mentioned above. Note the number of applications that are there compared to the number of applications that are launched when the operating system starts up. By looking at the number of icons in the system tray Note system tray is in the lower right-hand corner of the Windows screen next to the clock. and there will be a small icon It's in there If in the folder HKEY_LOCAL_MACHINESOFTWARE Contains folders of suspicious programs For example, the name of the company is spelled incorrectly. or grammatically incorrect Check to see if the program was installed by a virus or not. You may refer to the manual or search from the internet, etc. If you are sure that the program is actually a virus, then delete the said program from the registry. But keep in mind that modifying registry values ??can damage your system. Must use extreme caution. And before editing, you should back up the registry. Another way viruses use to spread themselves is by editing the registry associated with common file extensions to run the virus's own program. Examples of common file extensions include .EXE .DLL .COM, etc. In the Windows operating system, there is a registry key named /HKEY_CLASSES_ROOT. For storing values ??for files with which extension to run with which application. For example, files with the extension .DOC must be run with Microsoft Word (MS Word), etc. Backing up the registry is always a good way to help restore the system after a system malfunction resulting from registry modification errors. This may be caused by a virus editing itself or the user editing it themselves. A method for backing up the registry by exporting the registry values ??to a file. Or it's called exporting. This can be done by selecting the Registry menu -> Export Registry File as shown in Figure 5. A dialog will appear as shown in Figure 6. Then enter the name to save and press Save to complete the Registry backup process. Style When backing up the registry, retrieving the reserved registry for use can be done by selecting the menu Registry -> Import Registry File as shown in Figure 7 and a dialog as shown in Figure 8 will then appear. Select the file you want to run. Then press the button Open Figure 5 Show Registry Export Figure 6 Displays a dialog to select the file to use to back up the registry. Figure 7 Show how to import registry Figure 8 Displays a dialog to select recovery files. Other StartUp positions From what has been said above. There are other positions that viruses often use to start, such as in the System.ini and Win.ini files The virus modifies these files in the Windows directory (such as %Windows% or %Winnt%). The virus adds a line that says: "run=virus program name" or "load=Virus program name" Customization values ??that are important to the system can be edited with the Sysedit program. There is a way to run it by pressing the Start -> run button and then entering the word "sysedit" in the Open: field and press the OK button. A window will appear as shown in Figure 9 Note Customizing various settings Using the Sysedit program, you should back up each file first every time. Figure 9 Show Sysedit program There is also a folder that allows the operating system to execute applications contained in this folder every time the system starts. This folder can be accessed by Start -> (All) Programs -> Startup if there are unused applications or applications that are suspected of being viruses. In this folder, delete immediately All of the above methods for detecting viruses are You should study to understand and practice regularly to become proficient. And the important thing is to protect yourself from viruses in various ways. Such as updating various programs that are used as well as updating the database of virus programs etc.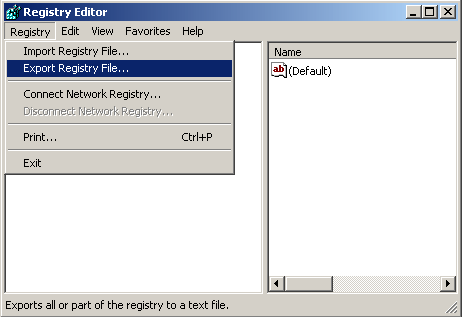
& lt; li & gt; & lt; a href = & quot; http: //www.securityfocus.com/infocus/1666" & gt; http: //www.securityfocus.com/infocus/166
& lt;/font & gt; & lt;/p & gt;